Types Of Privilege Escalation Attacks

Privilege Escalation Attacks Types Examples And Prevention Purplesec Privilege escalation is a cyberattack technique where an attacker gains unauthorized access to higher privileges by leveraging security flaws, weaknesses, and vulnerabilities in an organization’s system. it is the attempt to elevate access permissions by exploiting bugs, system flaws, human behaviors, configuration oversights, or weak access. There are two primary types of privilege escalation attacks that threat actors use: vertical and horizontal. while both types involve attackers attempting to gain unauthorized access to resources or perform malicious actions, how the attack is carried out can involve different approaches. vertical privilege escalation.

Investigating Windows Privilege Escalation 1 Quick Guide Privilege escalation is a step in the attack chain where a threat actor gains access to data they are not permitted to see. this guide to privilege escalation attacks covers the two main types. Privilege escalation attacks are a prevalent and complex threat, and any network can become a target. organizations need multiple defense strategies when any asset can become an entry point for intruders. understanding the privilege escalation process is an important first step toward prevention and defense against extensive network attacks. The solution— cynet network analytics continuously monitors network traffic to trace and prevent malicious activity that is otherwise invisible, such as credential theft and data exfiltration. 2. endpoint protection and edr. unauthorized access to endpoints is a common entry point in a privilege escalation attack. In cybersecurity, privilege escalation is the process by which an attacker gains access or permissions on a system that is at a higher level of privilege than what they had at the time of the initial compromise. attackers look to escalate privileges in one of two ways. they either do this horizontally or vertically.
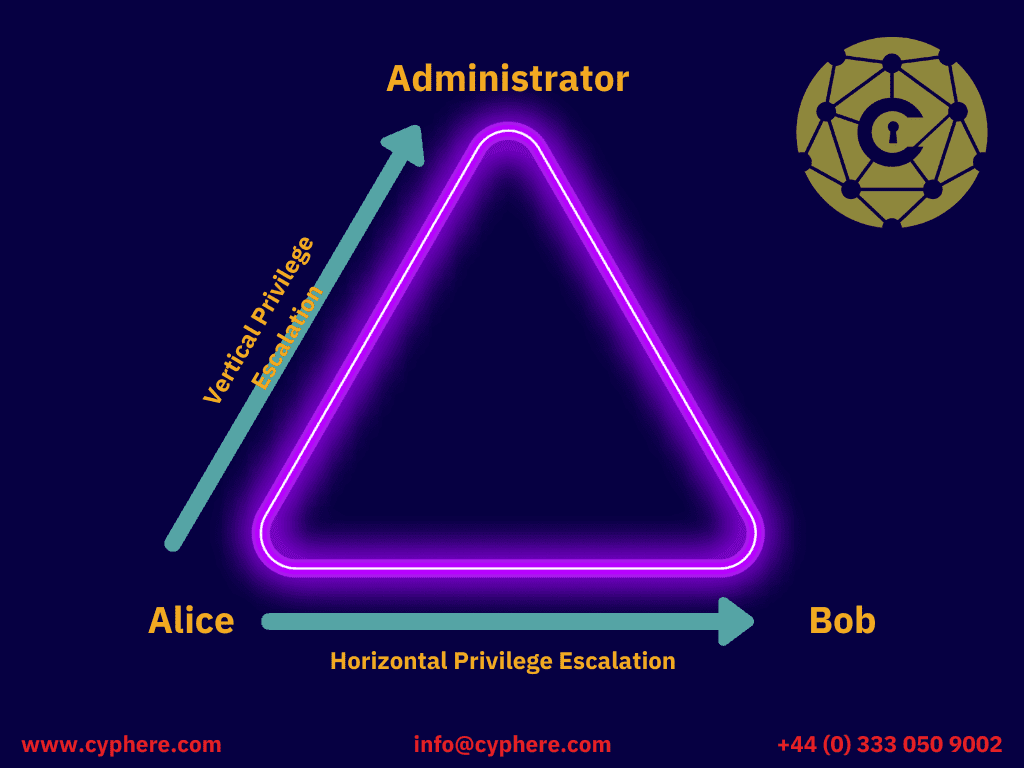
Privilege Escalation Attacks Types Examples And Defense The solution— cynet network analytics continuously monitors network traffic to trace and prevent malicious activity that is otherwise invisible, such as credential theft and data exfiltration. 2. endpoint protection and edr. unauthorized access to endpoints is a common entry point in a privilege escalation attack. In cybersecurity, privilege escalation is the process by which an attacker gains access or permissions on a system that is at a higher level of privilege than what they had at the time of the initial compromise. attackers look to escalate privileges in one of two ways. they either do this horizontally or vertically. Privilege escalation types. there are two types of privilege escalation: vertical and horizontal. in vpe (vertical privilege escalation), the attacker aims taking over an account that has system or root privileges. in hpe (horizontal privilege escalation) the hacker takes over an account and then tries to expand its control to other similar. Privilege escalation refers to the unauthorized elevation of user privileges, allowing an attacker to gain higher level access than originally intended. there are two main types of privilege.

Comments are closed.