Privilege Escalation Attacks Types Examples And Prevention Pdf

Privilege Escalation Attacks Types Examples And Prevention Pdf 5 common privilege escalation attack techniques and examples. now that you understand the two main categories of privilege escalation and why you must be vigilant in defending against these techniques, let’s look at five tactics that bad actors might use in such an attack. 1. credential exploitation. Ept away from a standard user. this form of a security breach is commonly known as a privilege escalation that facilitates illicit access to escalated rights and permissions beyon. what the user is entitled to.privilege escalation is one of the most commonly leveraged mechanisms in a modern cyber attack chain that results in unauthori.

Privilege Escalation Attacks Types Examples And Prevention Purpl Privilege escalation is a method that threat actors use to increase their access to systems and data that they aren’t authorized to see. often, they start their journey by stealing an initial. Privilege escalation is a cyberattack technique where an attacker gains unauthorized access to higher privileges by leveraging security flaws, weaknesses, and vulnerabilities in an organization’s system. it is the attempt to elevate access permissions by exploiting bugs, system flaws, human behaviors, configuration oversights, or weak access. The solarwinds supply chain attack highlighted the sophistication and potential impact of privilege escalation attacks. it underscored the need for organizations to implement robust security measures, including secure software development practices, supply chain risk management, privileged access controls, and continuous monitoring to detect and respond to privilege escalation attempts. Vulnerability. if such a privilege escalation attack succeeds, the attacker can operate the system with a privilege that is higher than the originally assigned one. for example, if an administrator’s privilege is acquired by an attacker through a privilege escalation attack, the attacker can avoid access.
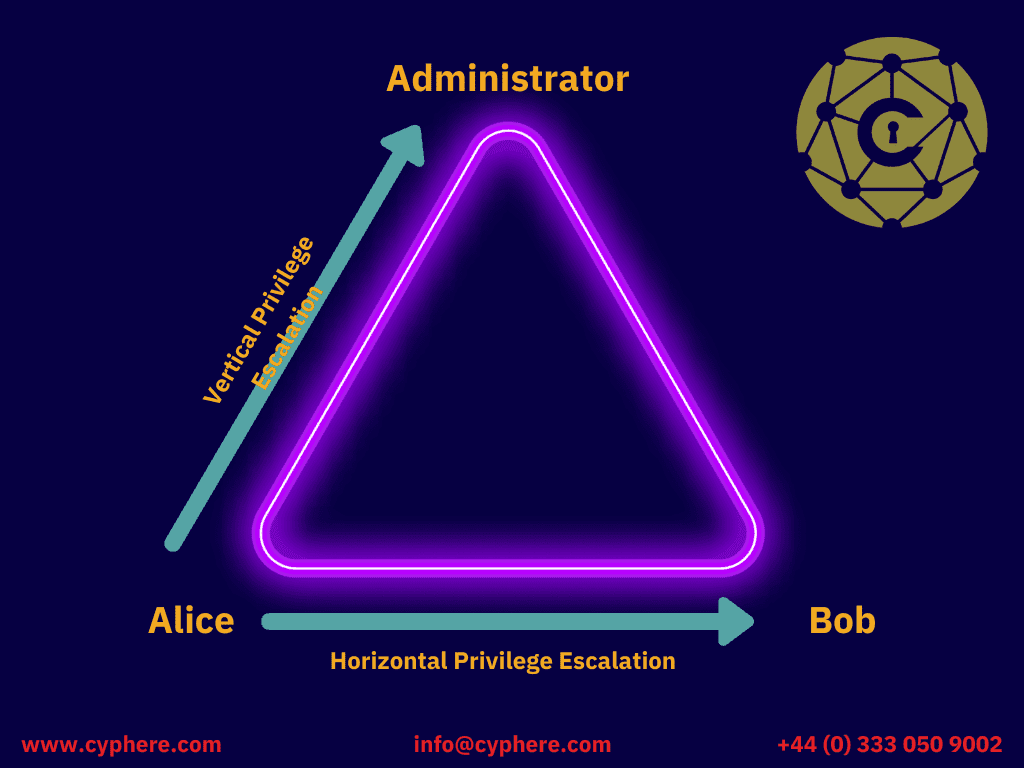
Privilege Escalation Attacks Types Examples And Defense The solarwinds supply chain attack highlighted the sophistication and potential impact of privilege escalation attacks. it underscored the need for organizations to implement robust security measures, including secure software development practices, supply chain risk management, privileged access controls, and continuous monitoring to detect and respond to privilege escalation attempts. Vulnerability. if such a privilege escalation attack succeeds, the attacker can operate the system with a privilege that is higher than the originally assigned one. for example, if an administrator’s privilege is acquired by an attacker through a privilege escalation attack, the attacker can avoid access. Introducing the proposed method in advance can prevent this type of attack by changing any process privilege that was not originally changed in a system call, regardless of the vulnerability type. Cyberattacks, especially attacks that exploit operating system vulnerabilities, have been increasing in recent years. in particular, if administrator privileges are acquired by an attacker through a privilege escalation attack, the attacker can operate the entire system and cause serious damage. in this paper, we propose an additional kernel observer (ako) that prevents privilege escalation.

Comments are closed.