Privilege Escalation Attacks Types Examples And Defence
Privilege Escalation Attacks Types Examples And Defense 5 common privilege escalation attack techniques and examples. now that you understand the two main categories of privilege escalation and why you must be vigilant in defending against these techniques, let’s look at five tactics that bad actors might use in such an attack. 1. credential exploitation. Privilege escalation attacks: types, examples and defence. when a system is breached, compromised or exploited, the attackers never stop after getting the initial access because it doesn’t give them privileged access. and the same thing goes in an offensive security assessment, i.e. infrastructure penetration testing or a red team assessment.

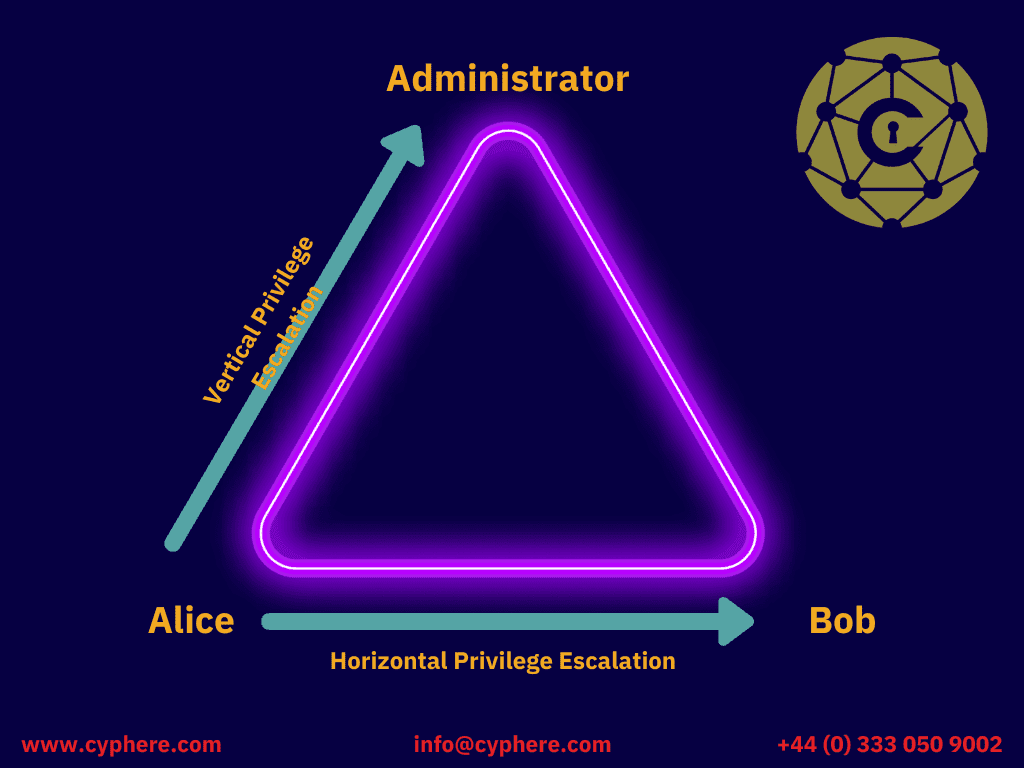
Privilege Escalation Attacks Types Examples And Defence Youtube In this video, we'll explore the various types of privilege escalation attacks, examples of them in action, as well as key areas for defence. get the knowled. Privilege escalation attacks exploit a bug or design flaw in operating systems or software applications. discover more about types, examples and defence of privilege escalation techniques. the post privilege escalation attacks: types, examples and defence appeared first on cyphere | securing your cyber sphere. Privilege escalation is a cyberattack technique where an attacker gains unauthorized access to higher privileges by leveraging security flaws, weaknesses, and vulnerabilities in an organization’s system. it is the attempt to elevate access permissions by exploiting bugs, system flaws, human behaviors, configuration oversights, or weak access. A privilege escalation attack is a cyberattack to gain illicit access of elevated rights, permissions, entitlements, or privileges beyond what is assigned for an identity, account, user, or machine. this attack can involve an external threat actor or an insider threat. privilege escalation is a key stage of the cyberattack chain and typically.

Privilege Escalation Attacks Types Examples And Prevention Purplesec Privilege escalation is a cyberattack technique where an attacker gains unauthorized access to higher privileges by leveraging security flaws, weaknesses, and vulnerabilities in an organization’s system. it is the attempt to elevate access permissions by exploiting bugs, system flaws, human behaviors, configuration oversights, or weak access. A privilege escalation attack is a cyberattack to gain illicit access of elevated rights, permissions, entitlements, or privileges beyond what is assigned for an identity, account, user, or machine. this attack can involve an external threat actor or an insider threat. privilege escalation is a key stage of the cyberattack chain and typically. Privilege escalation is a method that threat actors use to increase their access to systems and data that they aren’t authorized to see. often, they start their journey by stealing an initial. Another technique used in privilege escalation attacks is to modify the configuration settings of the domain. in particular, adversaries can escalate their privileges by modifying group policy objects (gpos). for instance, they might disable a gpo in order to gain the privilege of running a certain application.

Comments are closed.