Linux Red Team Privilege Escalation Techniques Kernel Exploits Sudo

Linux Red Team Privilege Escalation Techniques Kernel Exploits Sudo The final privilege escalation technique we will be exploring is the process of utilizing kernel exploits in order to elevate our privileges on the target system. this can be achieved performed automatically through the use of exploitation frameworks like metasploit, however, in this case, we will be exploring the process of identifying. In this video, i explore the process of elevating privileges on linux by leveraging kernel exploits, local accounts, and misconfigured sudo permissions.privi.
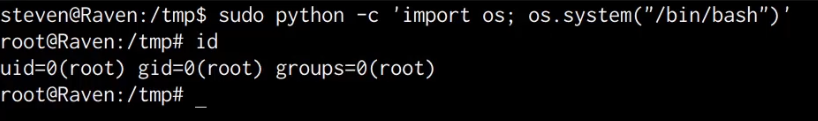
Linux Red Team Privilege Escalation Techniques Explore the process of elevating privileges on linux systems through kernel exploits, local accounts, and misconfigured sudo permissions in this 41 minute video tutorial. learn about privilege escalation techniques used by adversaries to gain higher level permissions on systems and networks. It is a useful shell script that gathers information about a linux host using a checklist of at least 65 items, such as kernel and sensitive users information, in order to find an escalation point. how to use in few steps: download linenum from github to your victim machine. edit the permissions: chmod x linenum.sh. A user account with admin like access. user accounts with access to a specific system or performs a specific function. the following is a list of key techniques and sub techniques that we will be exploring: 1. local accounts. 2. exploiting misconfigured sudo permissions. 3. kernel exploits. We have walked you through various linux privilege escalation techniques such as kernel and service exploits, understanding suid, managing scheduled tasks, and navigating password discovery. these techniques and tools, from exploiting misconfigured sudo permissions to leveraging vulnerable services, form an essential part of a pentester's toolkit.

Linux Red Team Privilege Escalation Techniques A user account with admin like access. user accounts with access to a specific system or performs a specific function. the following is a list of key techniques and sub techniques that we will be exploring: 1. local accounts. 2. exploiting misconfigured sudo permissions. 3. kernel exploits. We have walked you through various linux privilege escalation techniques such as kernel and service exploits, understanding suid, managing scheduled tasks, and navigating password discovery. these techniques and tools, from exploiting misconfigured sudo permissions to leveraging vulnerable services, form an essential part of a pentester's toolkit. Linux privilege escalation the typical techniques used are the following: kernel exploits ; application vulnerabilities; misconfigurations such as weak file permissions; abuse of sudo; abuse of setuid and setgid; cron jobs; poor passwords; first, attackers will explore linux systems to determine an attack path that won’t alert the security team. What vulnerability seem to affect the kernel of the target system? (enter a cve number) cve 2015 1328.
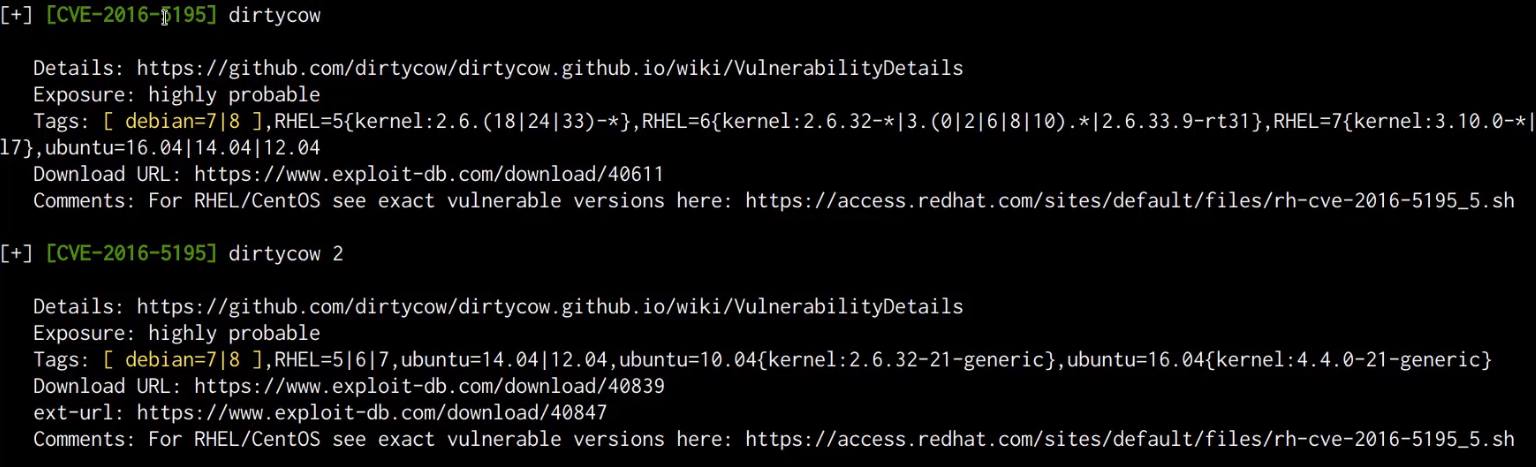
Linux Red Team Privilege Escalation Techniques Linode Docs Linux privilege escalation the typical techniques used are the following: kernel exploits ; application vulnerabilities; misconfigurations such as weak file permissions; abuse of sudo; abuse of setuid and setgid; cron jobs; poor passwords; first, attackers will explore linux systems to determine an attack path that won’t alert the security team. What vulnerability seem to affect the kernel of the target system? (enter a cve number) cve 2015 1328.
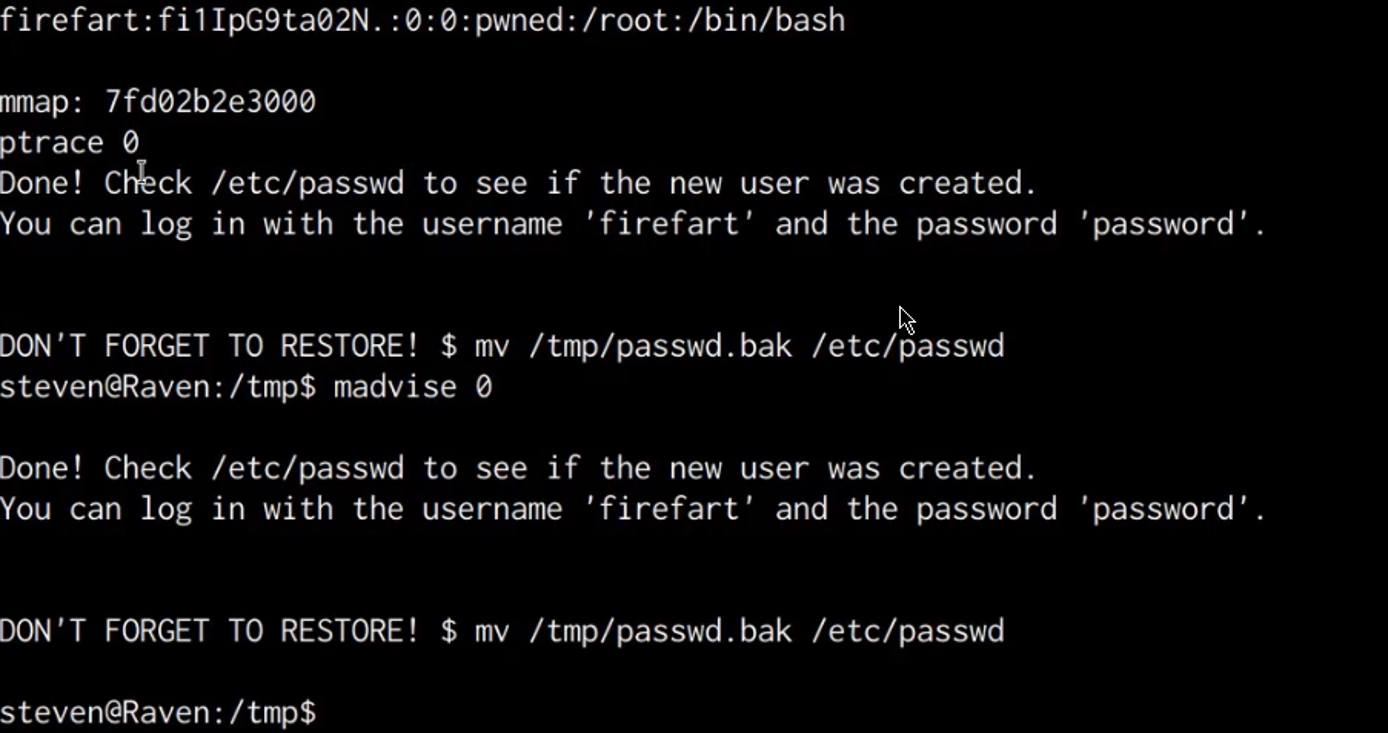
Linux Red Team Privilege Escalation Techniques Linode Docs

Comments are closed.