Linux Red Team Privilege Escalation Techniques

Linux Red Team Privilege Escalation Techniques Kernel Exploits Sudo The first privilege escalation technique we will be exploiting is the process of finding and cracking local account credentials in order to elevate our privileges. adversaries may obtain and abuse credentials of a local account as a means of gaining initial access, persistence, privilege escalation, or defense evasion. In this video in our hackersploit red team series, we will cover linux privilege escalation techniques. this includes obtaining root access, and exploiting permissions or binaries to achieve access. chapters: 0:00 introduction. 0:35 what we’ll be covering. 1:00 linux privilege escalation techniques.

Linux Privilege Escalation Techniques Red Team Series 9 13 Youtu It is a useful shell script that gathers information about a linux host using a checklist of at least 65 items, such as kernel and sensitive users information, in order to find an escalation point. how to use in few steps: download linenum from github to your victim machine. edit the permissions: chmod x linenum.sh. In this video, i explore the process of elevating privileges on linux by leveraging kernel exploits, local accounts, and misconfigured sudo permissions.privi. In this video in our @hackersploit red team series, we will cover linux privilege escalation techniques. this includes obtaining root access, and exploiting. The techniques outlined under the persistence tactic provide us with a clear and methodical way of obtaining establishing persistence on the target system. the following is a list of key techniques and sub techniques that we will be exploring: account manipulation. persistence via ssh keys.
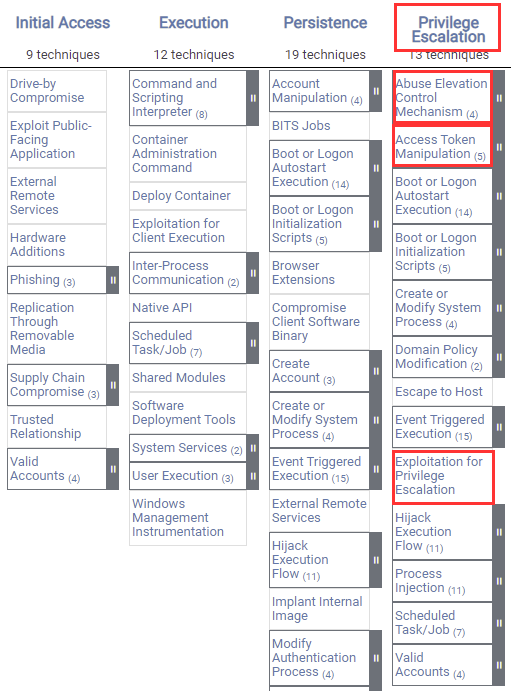
Linux Red Team Privilege Escalation Techniques Linode Docs In this video in our @hackersploit red team series, we will cover linux privilege escalation techniques. this includes obtaining root access, and exploiting. The techniques outlined under the persistence tactic provide us with a clear and methodical way of obtaining establishing persistence on the target system. the following is a list of key techniques and sub techniques that we will be exploring: account manipulation. persistence via ssh keys. Welcome to the linux privilege escalation section of this documentation. here, you'll find a comprehensive guide covering various techniques and methods to escalate privileges on linux systems. this information is curated to help security enthusiasts, penetration testers, and anyone interested in understanding how privilege escalation works in. Privilege escalation 10 tools. linpeas linux privilege escalation; winpeas windows privilege escalation; linux smart enumeration linux privilege escalation; certify active directory privilege escalation; get gpppassword windows password extraction; sherlock powershell privilege escalation tool; watson windows privilege escalation tool.

Comments are closed.