пёџ Extending Local Privilege In Linux Using A Kernel Exploit Rucore
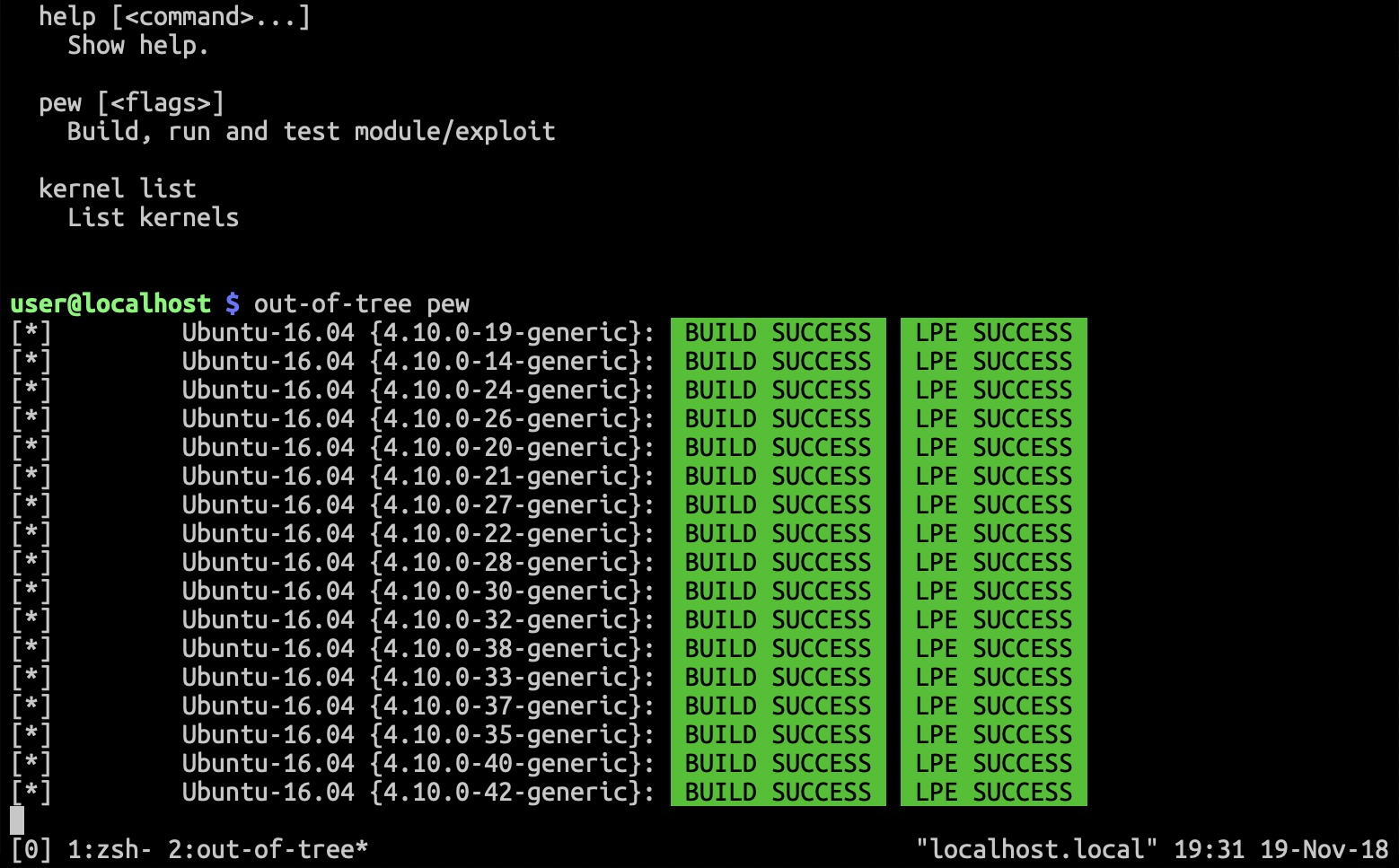
пёџ Extending Local Privilege In Linux Using A Kernel Exploit Step 2: delivery of the exploit to the target system. first, the exploit needs to be copied to the target machine. the easiest way to solve this problem is to set up a local web server (such as apache), connect to this server from the target system, and download the file. Step 2: compile the exploit, and execute it on one of the suid executables that we discovered for example, “ bin su”, to obtain the root privileges. > gcc dirtypipez.c o exploit > . exploit.
Linux Privilege Escalation Service Exploit Vrogue Co Assess exposure of the linux box to publicly known exploits: $ . linux exploit suggester.sh. show state of security features on the linux box: $ . linux exploit suggester.sh checksec. assess exposure of linux kernel on publicly known exploits based on the provided 'uname' string (i.e. output of uname a command):. Final thoughts. in this post we will be exploring various kernel exploits that can be used for linux privilege escalation from standard user to root. we will start by using various commands to find the kernel version on the victim host. from there, we will see multiple ways to find kernel exploits that will work against the kernel version we. Universal local privilege escalation proof of concept exploit for cve 2024 1086, working on most linux kernels between v5.14 and v6.6, including debian, ubuntu, and kernelctf. the success rate is 99.4% in kernelctf images. Task 5: privilege escalation kernel exploits find and use the appropriate kernel exploit to gain root privileges on the target system. terminate your previous machine. now, let's go through the steps of the kernel exploit methodology. 1. identify the kernel version. 2. search and find an exploit code for the kernel version of the target system.

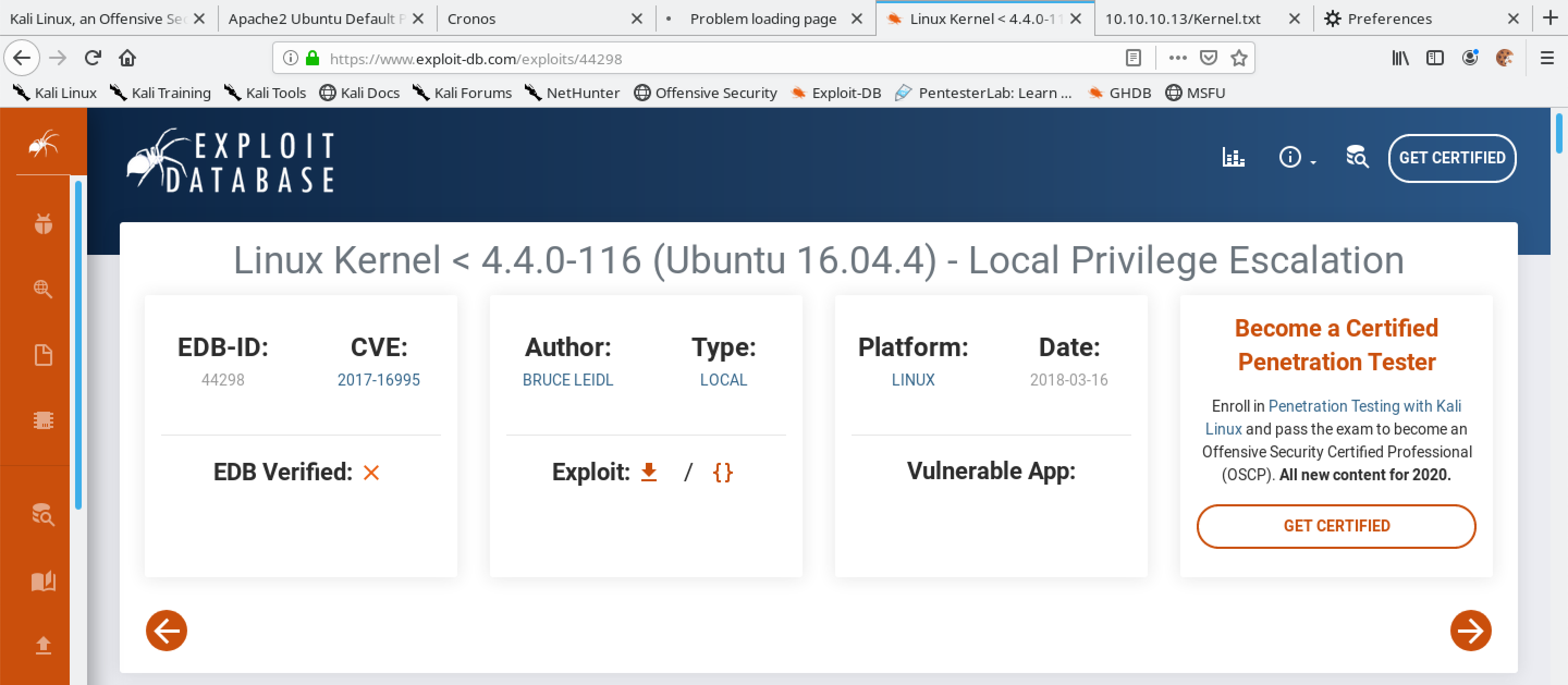
Linux Privilege Escalation Kernel Exploits Steflan S Security Blog Universal local privilege escalation proof of concept exploit for cve 2024 1086, working on most linux kernels between v5.14 and v6.6, including debian, ubuntu, and kernelctf. the success rate is 99.4% in kernelctf images. Task 5: privilege escalation kernel exploits find and use the appropriate kernel exploit to gain root privileges on the target system. terminate your previous machine. now, let's go through the steps of the kernel exploit methodology. 1. identify the kernel version. 2. search and find an exploit code for the kernel version of the target system. The first thing we need to do is identify the kernel version this operating system is running on. to do this, we can use multiple command that will return us the same result: uname a, cat proc version. here is a screenshot of the privilege that the user currently has. kernel version: `linux 3.13.0 24 generic` the next step is to look up the. Your objective is to gain root privileges on the target machine by exploiting a vulnerability in the linux kernel. follow these steps to complete the challenge: access the target machine: get the.

Local Privilege Escalation Flaw In Linux Kernel Allows Root Access The first thing we need to do is identify the kernel version this operating system is running on. to do this, we can use multiple command that will return us the same result: uname a, cat proc version. here is a screenshot of the privilege that the user currently has. kernel version: `linux 3.13.0 24 generic` the next step is to look up the. Your objective is to gain root privileges on the target machine by exploiting a vulnerability in the linux kernel. follow these steps to complete the challenge: access the target machine: get the.

Linux Privilege Escalation Service Exploit Vrogue Co

Comments are closed.